
Sponsored by Sumo Logic
Serverless computing, such as that offered by Amazon Lambda, is rising as organizations move to the cloud or modernize their applications by adopting cloud-native architectures. In fact, two in three companies are adopting serverless Lambda functions, according to Steve Dietz, field CTO at Sumo Logic, in an online talk. And he notes that serverless adoption has increased dramatically for Sumo Logic customers over the last few years.
It is no surprise why serverless is so popular. Organizations can build and run applications and services without managing the infrastructure itself. Other reasons serverless is so prevalent include the speed of execution and flexibility. The provider automatically scales resources to match the needs of the application or service. And the end-user organization only pays for compute time used. These factors are especially important for small-to-midsize businesses with emerging security teams.
Security issues with serverless
As serverless use becomes more popular, serverless computing security is becoming an important factor to consider. That is especially true when enterprises use serverless computing to power applications that interact with their legacy systems. There needs to be an assurance that the data and application code is fully secured in production.
AWS provides the basics for monitoring and logging for Lambda in the form of CloudWatch and CloudTrail. But more is needed. Specifically, the security team needs to know about the different microservices related to a cloud-native app. And the site reliability engineer (SRE) and CloudSec teams need to know if there are any threats related to the apps, their underlying services, or to the broader cloud environment. To address these issues, enterprises need good visibility into their modern environment.
What it comes down to is that an enterprise needs centralized logging and monitoring of its application. It needs metrics and logs to gain deep visibility into the performance of the Lambda applications. While metrics can alert a team to possible issues, logs provide deep visibility to identify threats and the root causes of issues. Ideally, by setting up custom alerts, companies can be proactive, catching security issues before they escalate. That is how enterprises should approach Lambda security.
An incident triggers concerns
Last year, security researchers at Cado Security discovered a malware strain designed to run in AWS Lambda serverless environments and mine cryptocurrency. Named Denonia, after the name the attackers gave the domain it communicates with, the malware used newer address resolution techniques for command and control traffic to evade typical detection measures.
Cado security researcher Matt Muir noted its significance. “It demonstrates how attackers are using advanced cloud-specific knowledge to exploit complex cloud infrastructure and is indicative of potential future, more nefarious attacks,” he said in a blog about the discovery.
One additional point raised is that while the malware “only ran crypto-mining software,” it did so at the expense of the enterprise paying the bill for the compromised services. Dietz noted a Twitter feed where a user’s credentials were compromised, and a scammer ran up $45,000 of server time to make $800 mining.
See also: How to Secure Your Cloud Platform and Be Ready for Your Next Audit
What’s needed for Lambda security
Denonia’s discovery was the shot across the bow, an industry wake-up call about the nuances of managing security in serverless environments.
The sheer volume of executions and the dynamic nature of Lambda functions can make it difficult to detect, investigate and respond to potential compromise. Under the AWS Shared Responsibility model, AWS secures the underlying Lambda execution environment, but it’s up to the customer to secure the functions themselves.
A unified security and observability platform that collects and brings together logs, metrics, and traces is needed to accomplish that. Bringing them together, and analyzing and interrogating them in real time, makes systems observable.
So, the first step is to collect the data. One of the ways to collect CloudWatch logs or Lambda logs is through CloudWatch and CloudTrail. CloudWatch monitors applications and infrastructure performance in the AWS environment. CloudTrail monitors actions in the AWS environment.
Additionally, Sumo Logic uses a mechanism called the open-source AWS Lambda extension, which runs as a lightweight process within the same execution environment as an organization’s Lambda functions. The extension uses the Lambda logs API to send platform, function, and extension logs to Sumo Logic. Dietz noted in his talk that this is very similar to the CloudWatch logs.
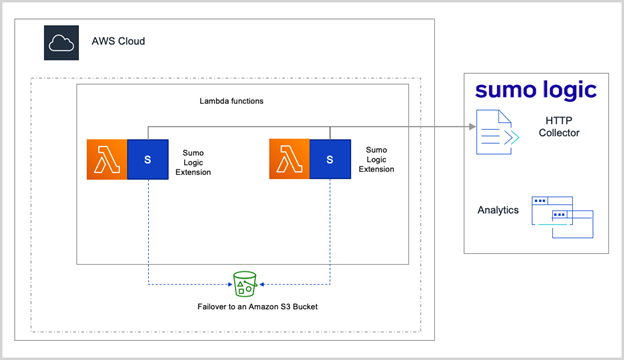
With such collection and real-time data analysis, the Sumo Logic platform provides a high-level overview of all Lambda functions and lets enterprises drill down into their Lambda functions. Additionally, this unified security and observability platform approach means that SRE teams, observability teams, and security operations have one dashboard that they all can use.
A final word about serverless security
With new threats like Denonia, organizations must have a platform that analyzes the many different services and streams of log data. For AWS, this means seamless integration with AWS CloudTrail, CloudWatch, VPC Flow, GuardDuty, SecurityHub, and more.
Security and development teams can leverage Sumo Logic’s unified platform to improve their security posture. Sumo Logic Cloud Security Analytics tracks changes in configurations and services without requiring hours of manual tracing and discovery efforts. It triages both security and application alerts and failures into a single organization queue.
Bottom line: the Sumo Logic unified security and observability platform can automatically detect and respond to severless threats, like those targeting AWS Lambda services. And via a single pane of glass, Sumo Logic helps emerging security teams secure serverless environments.

Salvatore Salamone is a physicist by training who has been writing about science and information technology for more than 30 years. During that time, he has been a senior or executive editor at many industry-leading publications including High Technology, Network World, Byte Magazine, Data Communications, LAN Times, InternetWeek, Bio-IT World, and Lightwave, The Journal of Fiber Optics. He also is the author of three business technology books.


